Is the Active-Flow docker instance running?
On the Active-Flow system run:
sudo docker ps
The output should include one line that ends in “active-flow”, indicating that the instance is currently up and forwarding udp port 2055. Example:
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
237ae0c61325 ac-hunter/flow "/home/flow/active-f…" 6 weeks ago Up 6 weeks 0.0.0.0:2055->2055/udp active-flow
Are inbound UDP port 2055 packets allowed by the firewall?
On the Active-Flow system get a firewall listing with:
sudo iptables -L INPUT -nxv
If the INPUT chain has no rules and a policy of ACCEPT (like the following):
Chain INPUT (policy ACCEPT 3130808 packets, 1218284392 bytes)
pkts bytes target prot opt in out source destination
$
that means all incoming traffic is allowed. If you do have rules in this chain and need help interpreting if that port is open or not, please send the above output to [email protected]
Are Netflow packets arriving on UDP port 2055 on the Active-Flow system?
The tcpdump program can show a single line output for each received packet. Here’s a sample command to report on received netflow packets, assuming that the primary network interface to the Internet is eth0:
sudo tcpdump -i eth0 -qtnp -c 10 'udp port 2055'
If Netflow records are arriving on that port, you’ll see output similar to:
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
IP a.b.c.d.57001 > e.f.g.h.2055: UDP, length 264
IP a.b.c.d.57001 > e.f.g.h.2055: UDP, length 120
IP a.b.c.d.57001 > e.f.g.h.2055: UDP, length 120
IP a.b.c.d.57001 > e.f.g.h.2055: UDP, length 312
IP a.b.c.d.57001 > e.f.g.h.2055: UDP, length 120
IP a.b.c.d.57001 > e.f.g.h.2055: UDP, length 312
IP a.b.c.d.57001 > e.f.g.h.2055: UDP, length 76
IP a.b.c.d.57001 > e.f.g.h.2055: UDP, length 1080
IP a.b.c.d.57001 > e.f.g.h.2055: UDP, length 1032
IP a.b.c.d.57001 > e.f.g.h.2055: UDP, length 456
10 packets captured
10 packets received by filter
0 packets dropped by kernel
This shows that the router at a.b.c.d is sending netflow records to the Active-Flow system at e.f.g.h .
If the tcpdump command prints “listening on eth0……” and stops, producing no more output, you may want to check your router configuration to make sure it’s feeding Netflow records to the right address and port. Please see the end of this document for a suggested configuration for Cisco ISR routers.
Are records making it out to log files?
Active-Flow saves its output to the “/opt/zeek/logs/’ directory tree. In particular, the currently generated logs are in “/opt/zeek/logs/flow-spool”.
To confirm that Active-Flow is saving records to disk, run the following on the Active-Flow system:
cd /opt/zeek/logs/flow-spool/
ls -al
tail -f conn.log
Within 60 seconds you should see new lines being added to this file. (Note: in the first 10 minutes after rebooting Active-Flow’s system or restarting Active-Flow, you may not see entries being added until the router sends the first template. Either wait for 15 minutes to pass, or run “sudo docker logs -f active-flow –tail=20” and look for lines like:
time="2020-03-03T21:47:37Z" level=error msg="Could not decode incoming data" error="No info template 2615 found for and domain id 256" fatal=false
to confirm that this is why you’re not yet getting logs. This issue should definitely disappear by the time the system has been up for 15 minutes.)
Are the compressed logs getting sent to /opt/zeek/logs/yyyy-mm-dd each hour?
At the end of each hour the active logs are compressed and moved to a directory for today’s date. To see them, run:
ls -al /opt/zeek/logs/`date +%Y-%m-%d`/
With the exception of the hour right after midnight you should see multiple files with the extension “.log.gz”. If you don’t, check with [email protected]
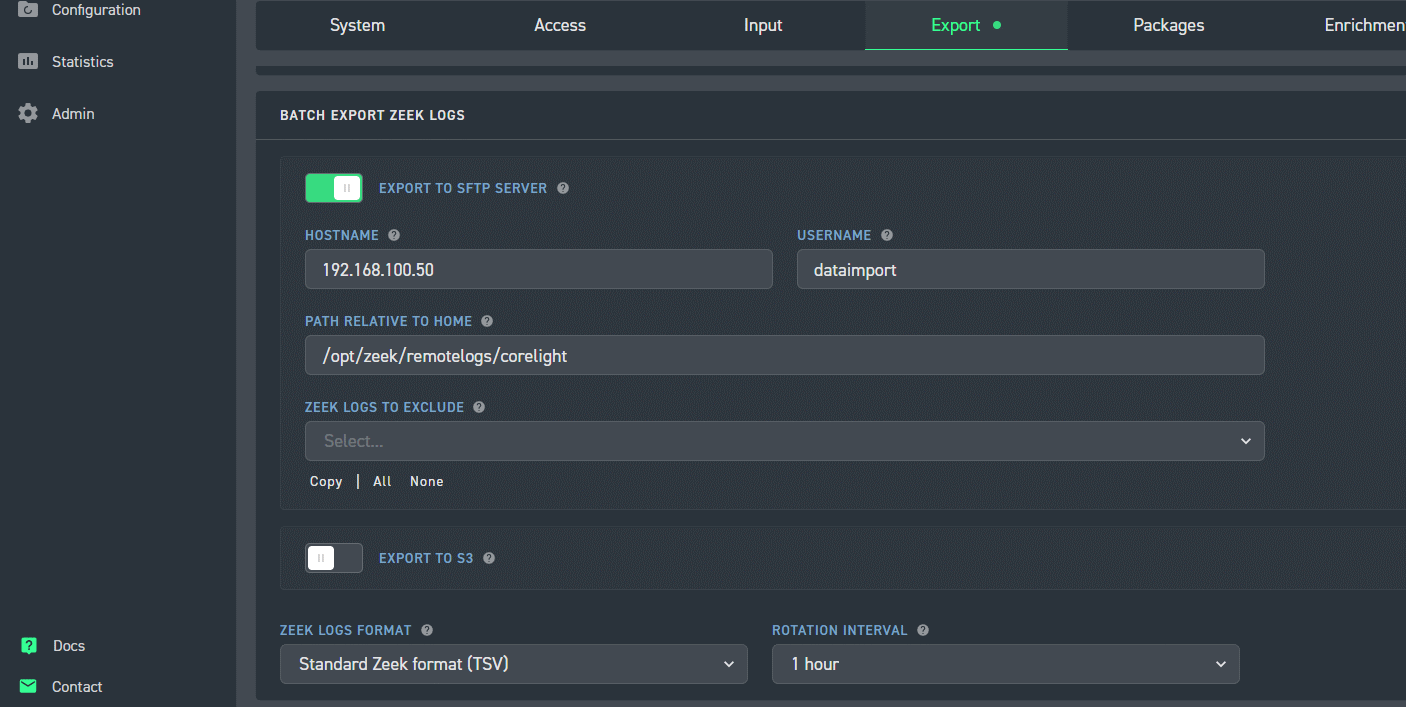
Are ssh connections allowed from Active-Flow to AC-Hunter?
Can you ssh from Active-Flow to dataimport@AC-Hunter without supplying a password?
Can you run zeek_log_transport.sh and push logs to AI-Hunter?
Is the cron job set up to automatically transfer logs?
Are the logs showing up on the AC-Hunter system in /opt/zeek/remotelogs/sensor-name/yyyy-mm-dd ?
The above 5 questions are covered in the FAQ at https://portal.activecountermeasures.com/support/faq/?Display_FAQ=861
Direct Link to this FAQ Item: https://portal.activecountermeasures.com/support/faq/?Display_FAQ=2722