Tuesday - 11/28/2023
Network Scanners
When you set up any network monitoring tool or packet sniffer it’s important to find a place on the network where you can see all the traffic. In the case of AC-Hunter, that includes all traffic going to or coming from the Internet.
Well, almost all traffic.
There’s one important exception to this: scanners. That includes any computers that go out thousands of times to other computers to make quick connections. These might be:
- – Checking to see if the remote system is responding at all,
- – Checking on the remote services on those machines to see if they’re returning valid results,
- – Checking on those remote services to see if they’re vulnerable to any known attacks, or
- – Simply scanning the internet to do some kind of Internet mapping
AC-Hunter is focused on regular connections to a small number of hosts, much like you’d find with a person browsing the web or a piece of malware calling home to a command and control server. The analysis we do to identify these hosts can get overloaded when one or more internal machines are placing extraordinarily large numbers of connections to outside systems, just like you’d find with internal scanning systems.
If you have systems like these, here’s what we recommend:
- – Lock down those systems carefully. They should be fully patched. They should also have as few open ports as possible; a good firewall that restricts client access to just a few admin systems would be great.
- – Tell Zeek to ignore them entirely. This blog post walks you through the needed steps: https://www.activecountermeasures.com/filtering-out-high-volume-traffic . Once you’ve made this change, Zeek will stop recording the outbound connections from the scanner(s).
It may take about a day for these to get filtered out from your AC-Hunter rolling database(s), but after that you should notice that the import happens more quickly and AC-Hunter may become more responsive.
PREVIOUS NOTIFICATIONS
Monday - 06/05/2023
Cosmetic Error With AC-Hunter 6.4.0 Installation
If you receive either of the following errors during the AC-Hunter 6.4.0 upgrade, please ignore them. The message is cosmetic only – there is no actual problem with the install.
You do not have a supported version of Docker-Compose installed. An unsupported version of Docker-Compose appears to already be installed. It will be replaced.
The messages showed up because a supporting tool was upgraded after we released AC-Hunter 6.4.0.
Thursday - 05/11/2023
Version 6.4.0 of AC-Hunter Has Been Released!
We’re pleased to announce AC-Hunter Enterprise Edition version 6.4.0! This version includes expanded operating system support, bug fixes, updated Zeek, Elasticsearch, Winlogbeat, Kibana, and docker-compose software, improvements to scoring, faster import speed, and internationalization improvements. The details are below; we encourage you to review them before upgrading as there are some upgrade considerations.
If any of the following are true we strongly recommend upgrading to 6.4.0:
– If you had to disable UserAgent processing in 6.3.0/6.3.1. Please re-enable UserAgent processing after the upgrade; instructions are below.
– If you use the Cyber Deception module on a Windows system whose primary language is not English.
– You are running into any of the problems mentioned below.
Note to BeaKer Users
To complete the upgrade to the new version of ElasticSearch, you’ll need to:
– Upgrade to Elasticsearch stack version 7.17.9:
– Upgrade Beaker using the AC-Hunter installer.
– Upgrade the Windows Agents on your Windows systems using install-sysmon-beats.ps1 – Verify that there are no upgrade conflicts using the Upgrade Assistant within the Kibana dashboard.
– Upgrade to Elasticsearch stack version 8.7.0:
– Upgrade BeaKer again using the AC-Hunter installer.
– Upgrade the WIndows Agents on your Windows systems again using install-sysmon-beats.ps1
Note that it is not required to upgrade to Elasticsearch 8.7.0 if you do not have an imminent reason to do so.
Operating System Support
We’ve had requests for additional operating systems on which one can run AC–Hunter. In this release we now offer these operating system as a beta test:
- AlmaLinux 8
- Centos 8
- RHEL 8
- Rocky Linux 8
- Ubuntu 22.04
Note: BeaKer has not been tested with these, so BeaKer still needs to run on a supported operating system (though AC-Hunter and the other modules can try these new OS’s if they run on a different machine). CentOS, RHEL, and Rocky 8 are not supported for Elasticsearch v8.7.0.
We believe we have the needed changes in place, but would love to hear if you use one of these and run into any issues. Please email us with any problem reports.
Improvements
We’ve updated the scoring to acknowledge that some beacons run for fewer than 8 consecutive hours, such as those on laptops that are only in an office for the workday. (*)
We reviewed the “connection count” portion of the scoring. It turns out that connection count is redundant and drives up the score unnecessarily, so this contribution was removed (*).
In the case where the hourly connection count is mostly uniform but has occasional bumps, we now use the coefficient of variation to smooth out the scoring. (*)
The Long Connections module in RITA now uses the Longest Total Duration instead of the Longest individual connection.
The manage_web_user.sh script that adds logins to the web server is now more verbose when a failure occurs, explaining why the account modification failed.
The “NeverIncludeDomain” setting in rita.yaml now applies to UserAgent and SSL/TLS entries on import.
The import speed for UserAgents has been improved dramatically. On a network where there are large numbers of UserAgents, this import happens many orders of magnitude faster. If you followed our temporary workaround for this issue (see “Excessive Numbers of JA3 Hashes Slowing Data Import” on https://portal.activecountermeasures.com/ ), you can revert this change after upgrading to 6.4.0 by running:
sudo nano /etc/AC-Hunter/rita.yaml
Scrolling down to the block:
UserAgent: Enabled: false
and changing “Enabled: false” to “Enabled: true”. Make sure to leave exactly 2 spaces to the left of “Enabled: true”.
Finally, running
hunt down hunt up -d --force-recreate
If you ran into this problem in previous versions, you must say yes when prompted to reimport databases during the AC-Hunter upgrade.
The import_pcaps.sh script now uses Zeek 4.2.0 for processing pcap files. It correctly handles a common case of incorrect checksums in pcap files. It also includes the reserved networks (starting with 10, 192.168, and 172.16 through 172.31) as defaults for Zeek’s “local_nets” setting.
We’ve made some internal changes on how docker-zeek and zeek-log-transport are made available. The Zeek installer we deploy with install_acm.sh is now available as an open source download at https://github.com/activecm/ACH-Zeek/ . Additionally, Zeek-Log-Transport is now available as an open source download at https://github.com/activecm/zeek-log-transport/ .
The Winlogbeat software used in Espy and Beaker has been updated. The Elasticsearch and Kibana software used in BeaKer has also been updated. Both of these releases offer upgrades to versions 7.17.9 and 8.7.0 for all three ELK stack technologies.
docker-compose has been upgraded to version 2.
The EventService module now runs correctly when the default language on the Windows system is not English. Many thanks to Johannes Muller-Lahn for this improvement.
Syslog alerts are now more easily parsed as they no longer show a field if there’s no associated value.
New installations of Zeek deployed with install_acm.sh will write out a log called open_ssl.log. This log tracks the TLS details for connections written to open_conn.log.
SSL log filtering now honors the “AlwaysInclude” and “NeverInclude” lists.
DNS log filtering now filters out external->internal traffic.
We’ve updated the underlying Linux software for many of our services.
* Note that any changes to the scoring used in AC-Hunter go through a rigorous set of regression tests against both malicious and benign traffic to ensure that the changes improve the scoring in question but do not negatively affect other types of traffic.
Bug Fixes
In the deception module, the tokens that were created earlier were incorrectly deleted during an upgrade. We’ve fixed this so that upgrades to versions 6.4.0 and higher will not delete these any more.
The configuration syntax for logging in version 6.3.0 effectively disabled logging to the syslog server on the Docker host. To avoid this we’ve added a configuration choice so you can explicitly enable and disable alerting. Alerting will be enabled by default as it was prior to version 6.3.1. If you do not use alerting, disabling it can provide potential performance improvements. To set these, run:
sudo nano /etc/AC-Hunter/config.yaml
The “Enabled” fields go in these sections. Please make sure the fields are indented with the same number of spaces as the lines around them (“Alert:” should be at the left edge of the file, and “Enabled: true” should be indented with exactly 2 spaces.)
Alert: Enabled: true
Once you’ve made this change, please run:
hunt down hunt up -d --force-recreate
The import process now correctly handles truncated IP addresses in a log file.
The SNI connection analysis was being performed even when SNI beacon analysis was disabled – this has been fixed.
And a few surprises!
ACM has contributed most of the content for the 4th issue of Prompt# , called “On the Hunt“. You can view the zine online or request a free mailed printed copy at that link.
If you use bro-cut or zeek-cut to analyze Corelight and Zeek logs, we’ve written a similar tool called zcutter . Like zeek-cut zcutter works with tsv (tab-separated column) logs, but also supports json-formatted logs (as well as converting between the two). More details and downloads are at zcutter’s github repository .
We’ve been creating new training videos on using AC-Hunter. Some of them have already been edited and uploaded to https://www.youtube.com/@ActiveCountermeasures . Others will be showing up over the next few weeks.
Questions?
As always, if you have any questions about any of the above, please feel free to contact us.
Download AC-Hunter v6.4.0 here:
For details of how to install AC-Hunter, please see the Install Guide PDF included in the tarball or the Documentation section of this website. If you run into any issues, feel free to contact us.
Enjoy and Happy Threat Hunting!
– The Active Countermeasures Team
(For our AC-Hunter Hosted SaaS customers, we will be performing upgrades to v6.4.0 on that platform in the coming days.)
Friday - 02/17/2023
Excessive Numbers of JA3 Hashes Slowing Data Import
We’ve received reports from AC-Hunter 6.3.0 customers who are finding that the import process is grinding to a halt; the work required each hour is taking far more than an hour to complete. The end effect is that the rolling database(s) will not have current information; you’ll commonly see a date range (in the upper right of most tabs) that’s a few hours or days out of date.
TL;DR (or short version)
If your logs are being correctly imported into AC-Hunter 6.3.0, you do not need to continue with this note and you do not need to take any action.
If you’re finding that AC-Hunter is falling behind at importing data, please read on.
The UserAgent processing may be taking too long to complete. The very likely workaround is to disable UserAgent processing until we have a permanent fix available. Log in to your AC-Hunter system and run:
sudo nano /etc/AC-Hunter/rita.yaml
In that file, uncomment or add the following lines:
UserAgent: Enabled: false
“UserAgent:” needs to be at the far left edge of the file, and “Enabled: false” needs to be indented with exactly 2 spaces. Save by pressing Ctrl-O , then exit with Ctrl-X .
Once done, run:
hunt down hunt up -d --force-recreate
Within 2-6 hours after the above change, AC-Hunter should be able to catch up again. Within 25 hours you should have a complete set of data to analyze, with the exception of the UserAgent tab which will have no results.
We’re investigating the best way to provide a permanent fix for this and we will provide an announcement when that fix is ready.
More Detail
The UserAgent module works off an assumption that most computers will have a very small number of ways they negotiate TLS connections (such as HTTPS encrypted connections to web servers). These negotiations are summarized in what’s called a “ja3 hash”. Most computers negotiating encrypted connections will have a small number of these hashes, allowing AC-Hunter to quickly summarize them.
In recent releases we’re seeing huge numbers of hashes show up, both for individual systems and for networks as a whole. Where we expected to see hundreds to low single digit thousands of hashes for an entire network, now we’re seeing tens of thousands or hundreds of thousands of hashes in a given day at some sites. The UserAgent code in AC-Hunter is not able to efficiently process such massive quantities of data, and the import process grinds to a halt.
To test if you’re seeing this issue, we have a test script that will count how many ja3 hashes show up in a given day (using “yesterday” as that should be a complete set of Zeek/Corelight logs.) Please log in to your AC-Hunter system and run the following commands. Note that the second command could wrap on this page, but everything from “wget …” to “…/02/day-hashes.zip” is one command:
cd wget -O day-hashes.zip https://portal.activecountermeasures.com/wp-content/uploads/2023/02/day-hashes.zip unzip day-hashes.zip chmod 755 day-hashes.sh ./day-hashes.sh
The only change this script will make is automatically installing a utility called “jq” to process json logs if your system uses that format.
The script will report a block of lines like the following (one block for each sensor):
Checking /opt/zeek/remotelogs/sensor_name/2023-02-15 24 ssl logs found, good. These appear to be tsv-format logs. Please be patient, this may take a few minutes. You appear to have 1104295 unique ja3 hashes over all systems in yesterday's logs. This number appears very large - please contact [email protected] with this entire output.
If you have large numbers of unique ja3 hashes – as we see in the 5th line above – you’re likely running into this problem, and we encourage you to disable the UserAgent processing using the steps at the top of this note.
As always, if you have questions about the information above, please contact us.
Thursday - 01/26/2023
Post 6.3.0 Release Issue
AC-Hunter Install Issue on Ubuntu 20.04
During an install on a completely patched Ubuntu 20.04 system, you may encounter a series of error messages, each of which ends with the lines:
... File "/usr/lib/python3/dist-packages/OpenSSL/crypto.py", line 1573, in X509StoreFlags CB_ISSUER_CHECK = _lib.X509_V_FLAG_CB_ISSUER_CHECK AttributeError: module 'lib' has no attribute 'X509_V_FLAG_CB_ISSUER_CHECK'
This appears to be an issue related to python libraries that were updated after AC-Hunter v6.3.0 was released. We’ll have a permanent fix in the next release.
The current workaround is to run the following command from the AC-Hunter command line:
sudo -H python3 -m pip install pyOpenSSL --upgrade
Once you’ve run this you can restart the AC-Hunter installation and the install should complete.
Thursday - 01/19/2023
Version 6.3.0 of AC-Hunter Has Been Released!
While our 6.2 releases provided a large collection of new features, fixes, and general improvements to AC-Hunter, we found some issues that showed up in live installations after the release. Our future work was put on hold while the entire development team worked on fixes for these issues, now available as AC-Hunter 6.3.0 . It can be downloaded from your portal account at https://portal.activecountermeasures.com/my-account/downloads/ .
Short Summary
– 6.3.0 fixes a number of performance issues and bugs in 6.2.0 and 6.2.1.
– We strongly recommend anyone using 6.2.0 or 6.2.1 upgrade to 6.3.0.
– If you are using LDAP authentication, please see the LDAP note below.
– If you regularly use BeaconsFQDN, please switch over to the BeaconsWeb tab instead.
The Full Details
Bug Fixes
– On networks with heavy traffic we may run into a limit in the Mongo database server. Mongo limits its documents to 16MB. We’ve implemented new thresholds and limits and increased the rate of queued operations to avoid this issue. Because the number of DNS queries from an internal DNS server regularly exceeds this internal limit we’ve replaced the maximum DNS count scoring on the Dashboard and in alerts with an overall “C2 over DNS” warning banner.
– When the above problem showed up this would occasionally lead to databases that didn’t show up in the database list and so could never be deleted. We now delete these orphaned databases if an error occurs when they’re being created. If you suspect you may have orphaned databases, “rita clean” can be run at the command line to remove them.
– On some systems the daily snapshots were not being created or were taking days to create. This also appears to be related to the above Mongo database limit and has been handled.
– There were some isolated cases where safelist entries were not being applied. We believe we’ve addressed the issue behind this. If any safelist entries are incomplete or mis-formed, we’ll either clean up the entry so it can be imported or skip it and explain why in the web interface.
– If 2 or more web interface accounts were added where the only difference was the character case of a letter, the login process might choose the wrong account. This would include a situation where one of the accounts was added by hand and the other account came from LDAP. This has been fixed. If you have created a local web login whose name is (almost) identical to an LDAP account name (differing only in upper/lower case), you’ll need to delete the local login as it takes precedence over the LDAP account, and will block LDAP synchronization entirely for the conflicting email address.
– The importer code would occasionally hang during Host aggregation if no local hosts were found. This has been fixed.
– The LDAP synchronization code would occasionally fail, leading to a lack of synchronization with the LDAP server. This has been fixed.
– The Max Beacon score now recognizes when a beacon score goes down and correctly displays it.
– The list of potential connections on the left side in beacons would occasionally get a duplicated list of connections. We’ve fixed the issue that caused this.
BeaconsFQDN is now BeaconsWeb
We’ve had a few comments that having 4 different Beacons-type screens is confusing, and we agree. BeaconsFQDN was our first pass at Beacon analysis that allowed safelisting by hostname (also known as FQDN, or Fully Qualified Domain Name). We added the “Beacons Web” tab as a replacement for BeaconsFQDN that focuses on the HTTP and HTTPS/TLS traffic that is heavily used for C2 channels. Some of the core changes that have gone into 6.3.0 focus on the last pieces needed to make BeaconsWeb a replacement for Beacons FQDN, so we’re retiring BeaconsFQDN in this release.
There are a few advantages to switching to BeaconsWeb. First, BeaconsWeb is far more efficient to import, meaning that AC-Hunter will be able to keep up with more heavily loaded networks. Second, the domain name/hostname Safelist entries you’ve already created in BeaconsFQDN will continue to work with BeaconsWeb.
As a side note, any beacon traffic that is not HTTP or HTTPS-based will be found in the “Beacons” tab.
New Features
– Alienvault added as an investigation menu source for hostnames. If you are upgrading to AC-Hunter 6.3.0 (as opposed to installing a new instance), you can edit /etc/AC-Hunter/config.yaml , scroll down to the DomainSources section, and add the following two lines after the “Google:…” line (making sure they are indented with the same number of preceding spaces as the Google line:
# AlienVault Open Threat Exchange provides IOCs and threat intel
AlienVault: https://otx.alienvault.com/indicator/hostname/${fqdn}
Once you’ve made that change, run:
hunt up -d --force-recreate
– When you’re safelisting on the Beacons tab you’ll be offered the chance to do your safelisting by hostname (Fully Qualified Domain Name).
– Release 6.2.1 included an update to the scoring on the Beacon tab that raises the score for likely malicious traffic (without also raising the scores for benign traffic). This change means you have fewer connections to search through to find the malicious ones. Those changes are now also applied to BeaconsProxy and BeaconsWeb.
Improvements
– In massive databases it’s possible to have hundreds or thousands of pages of results; far more than any person would go through, especially when the most interesting results are at the top of the list. We’ve limited the number of pages of results to 100. This speeds up the user interface considerably.
– Long client signatures are now correctly truncated.
– Proxied connections that end up connecting to an internal host are no longer processed (since Threat Hunting focuses on connections going to/from external hosts).
– When safelisting by hostname, the default is to safelist for the entire internal network instead of a single internal IP (though you can still switch to a single IP address if appropriate).
Importing Databases
During the upgrade to 6.3.0 we’ll upgrade the rolling databases to address the above issues. We won’t upgrade the daily snapshots as this can take a long time, but you have the ability to re-import any snapshots (after the install is finished) as long as you have the zeek logs for them. Please see https://portal.activecountermeasures.com/support/faq/?Display_FAQ=7732 for the steps.
Closing Thoughts
We apologize for the bugs that were uncovered in 6.2 releases. We’ve updated our QA process to include testing on larger data sets that would have triggered the above issues, so we expect that we will be able to catch similar problems in future releases during development or QA.
If you have any questions about any of the above, please feel free to contact us.
Download AC-Hunter v6.3.0 here:
For details of how to install AC-Hunter, please see the Install Guide PDF included in the tarball or the Documentation section of this website. If you run into any issues, feel free to contact us.
Enjoy and Happy Threat Hunting!
– The Active Countermeasures Team
(For our AC-Hunter Hosted SaaS customers, we will be performing upgrades to v6.3.0 on that platform in the coming days.)
Wednesday - 11/02/2022
Notice About the 11/01/2022 OpenSSL Vulnerability
Background
The openssl project released an advisory about 2 issues with the openssl library. Versions of this library are used in the AC-Hunter suite, as well as the underlying Linux operating system on which that suite runs.
Short Version
AC-Hunter does not need an upgrade to handle this issue. As always, it’s a good idea to apply patches to the underlying Linux distribution regularly just in case the issue needs to be fixed in the underlying operating system.
Openssl Locations
AC-Hunter Software Suite
AC-Hunter uses openssl 1.1 as provided by docker containers, which are not vulnerable to either openssl issue.
Ubuntu Linux Base Distribution
Only Ubuntu 22.04 and 22.10 are vulnerable to this issue. To apply patches for it, run:
sudo apt update sudo apt upgrade sudo reboot
Centos Linux/Redhat Enterprise Linux (RHEL) Base Distribution
RHEL 9’s openssl package appears to be the only one affected by these 2 advisories (https://access.redhat.com/security/cve/CVE-2022-3602 and https://access.redhat.com/security/cve/CVE-2022-3786). RHEL 9 is not a supported OS for AC-Hunter at this time.
No action is needed for the supported RHEL 7 or Centos 7 Linux distributions.
This advisory is dated November 1, 2022 at 9:37pm Eastern US time. This, and any updates, will be posted to https://portal.activecountermeasures.com/ .
References:
https://www.openssl.org/news/secadv/20221101.txt
https://lists.ubuntu.com/archives/ubuntu-security-announce/2022-November/006893.html
https://access.redhat.com/security/cve/CVE-2022-3602
https://access.redhat.com/security/cve/CVE-2022-3786
Friday - 09/30/2022
AC-Hunter 6.2.1 Is a Bug Fix Release Only
1. Version 6.2.0 was supposed to include a configuration setting that would disable processing Incoming connections, dramatically reducing the amount of traffic that would need to be processed. The change was unfortunately not included in the final release of 6.2.0 . AC-Hunter 6.2.1 includes this change to the default of “FilterExternalToInternal”. If you’d prefer to make this change by hand rather than reinstalling AC-Hunter, we show the needed steps in the Bug report. Please see the following link for the 6.2.0 FilterExternalToInternal bug report.
2. The safelisting code in 6.2.0 is running into a problem with safelist entries that do not have matching data in a given database. This issue will cause the safelist to half-heartedly apply to any dataset that does not have connections between a safelisted IP pair. Upgrading to v6.2.1 will automatically resolve this issue.
We apologize for these problems.
Friday - 09/30/2022
Bug – Safelist Processing
We uncovered a bug in safelist processing in AC-Hunter 6.2.0 . The safelist program appears to have an issue with safelist entries that no longer match data in one’s data set. For example, if you add an IP pair safelist entry from a laptop in your building to an external server but that laptop is not in the office because its owner is on vacation, the safelist code malfunctions and only partly applies the safelist to that recent dataset.
This issue does not affect versions 6.1.0 and lower.
What This Means
You may run into situations where safelist entries are not being applied. This means you’re being presented with potential threats that should have been safelisted.
Do I Need To Do Anything?
Because effective safelisting is so important in reducing your effort in Threat Hunting, we strongly recommend fixing the issue by upgrading any AC-Hunter 6.2.0 systems to 6.2.1 . There is no workaround available for AC-Hunter 6.2.0 .
Upgrading to Fix the Issue
You can upgrade to version 6.2.1 which contains the fix. Version 6.2.1 is available at https://portal.activecountermeasures.com/my-account/downloads/ .
More Questions
As always, if you have any questions about this, please contact support at https://portal.activecountermeasures.com/support/ .
Tuesday - 09/27/2022
Version 6.2.0 of AC-Hunter Has Been Released!
Summer Codin’
When asked if they would prefer to be spending their time on a warm beach somewhere with a nice cool beverage, our developers replied “No! We’d rather be working on making AC-Hunter a better product!” At least we think that’s what they said. Either way, it’s a real privilege to work with such dedicated coders.
Before Upgrading
Before you run the installer to upgrade to 6.2.0, please go into the web interface, click on Dashboard, then click on the gear in the upper right, select “Safelist” and press “Export”. This will back up your current Safelist in case there are any issues with the upgrade. (It’s a good idea to do this at least weekly and before each upgrade in general.)
Safelist Application Changes
We’ve made a major change to how safelists are applied. Please be sure you understand this change prior to upgrading.
Historically, when you’ve created a safelist entry based on a Fully Qualified Domain Name (FQDN), we’ve also applied the safelist to the IP address(es) that map to that FQDN. This made sense from a performance perspective. The problem, however, is that many of the FQDNs you may wish to safelist use CDN services. If an attacker can pass their C2 traffic through the same CDN server, the C2 channel could potentially be missed.
For example, imagine you want to safelist the servers associated with Windows Notification Services because they are expected and can be pretty noisy. You create a safelist entry that ignores all traffic going to “*.wns.windows.com”. Microsoft uses Akamai for CDN services, so with previous versions this could potentially safelist not just Microsoft IP addresses, but Akamai IP addresses as well.
Now let’s assume an attacker sets up a C2 server and subscribes to Akamai services. It’s possible that the IP address a compromised system calls home to is the same IP being used by Windows Notification services. With the above safelist entry implemented, this could cause the C2 channel to go undetected.
With this new version, safelisting a FQDN only applies to that FQDN. So in the above example, connections to the Akamai CDN that contained “*.wns.windows.com” in the server name field of the HTTP or HTTPS negotiation would be safelisted. All other connections to the same CDN IP addresses would not be safelisted.
We feel this change will help secure your environment but wanted to be sure you are clear on the changes.
External to Internal Traffic Changes
AC-Hunter versions up to 6.1.0 treated Incoming traffic from the Internet and Outgoing traffic from your networks the same way – both were analyzed to look for possible threats. The problem with the Incoming traffic is that port scans from the outside world could lead to thousands of entries that fill up the display, making it harder to identify actual Threats.
Starting in version 5.4.0 we offered the ability to disable Threat processing of Incoming traffic. Still, this option was left at a default of false, meaning that Incoming traffic continued to be analyzed by default.
With version 6.2.0, we now disable this processing of Incoming connections by setting “FilterExternalToInternal” to “true” by default. If you wish to continue to analyze Incoming connections, you’ll need to see “Analyzing incoming traffic” in the AC-Hunter Install Guide, which shows you how to set “FilterExternalToInternal” to “false” if you wish to return to the way version 6.1.0 and below operated by default.
New Features
-In this release, we’ve revisited many aspects of how we score threats. In particular, we’ve focused on malicious traffic types that may have scored in a middle range and have raised their scores so that they’ll show up higher in the list. We’ve done this in a way that won’t also raise the scores for non-threat traffic.
-We have a new module for identifying beacons – BeaconsWeb. This identifies the remote system name by the hostname embedded in the TLS (encrypted web) header. (The other modules identify the system name by DNS lookups, which are not effective when the DNS lookup itself is encrypted.)
-In beacons fqdn, beacons web, beacons proxy, and client signature, searching by IP or FQDN (Fully Qualified Domain Name, aka hostname) is now available. In the dns module, searching by FQDN is now available too.
-We’ve had customer requests for some more types of safelisting, and have added the following: IP -> FQDN, Subnet -> Subnet, and Subnet -> FQDN safelisting.
-The AC-Hunter installer now supports a “non-interactive” mode when upgrading. For example, to upgrade zeek (currently on 10.0.0.20) and AC-Hunter (currently on 10.0.0.21) without asking for user input, you can run:
./install_acm.sh zeek 10.0.0.20 achunter 10.0.0.21 --non-interactive
Please see the AC-Hunter Install Guide for more details.
-If you have 2 or more AC-Hunter instances that all send alerts, it wasn’t clear in previous releases which one sent the alert. We now include a URL back to the original AC-Hunter system if you set the “Hostname:” field in user.yaml ‘s “Alert:” section.
-Based on customer feedback, we’ve swapped the views in the Long Connection tab. In version 6.1.0 and below “Longest Duration Analysis” was the default view 1. In 6.2.0 and above, “Total Duration Analysis” will be the default view 1 so you’ll jump right to the total amount of time over a day (instead of the length of the single longest connection.)
-The alert subsystem in 6.1.0 and below would send an alert on any change in score. This could lead to alert fatigue. 6.2.0 now offers the “MinimumReportableScoreChange” value, which defaults to 5. Any score change that’s between -4.9999 and +4.9999 will not get an alert, though score changes greater than 5.0 (or less than -5.0, if you report on decreased scores) will continue to send alerts.
-The AC-Hunter package now includes /usr/local/bin/rita_delete_old_dbs.sh , which can be used to automatically delete databases older than N days. This can be run at the command line or from cron (to automatically prune old databases every day.) For example:
/usr/local/bin/rita_delete_old_dbs.sh 180
will do a dry run and report on what databases older that 180 days would have been deleted, and:
/usr/local/bin/rita_delete_old_dbs.sh 180 -a
will actually delete those same databases. There are notes at the top of the script on how to install it as a cron (regularly scheduled) task. For more coverage of how to either manually or automatically delete Zeek logs and databases, please see https://portal.activecountermeasures.com/support/faq/?Display_FAQ=4970 .
-For auditing, we now log two event types – AC-Hunter logins and changes to the safelist – to /var/log/ACM/events.log . This may be useful for auditing.
-Syslog alerts now include the remote IP address/FQDN of the highest scoring beacon for the following: IP beacon, FQDN beacon, Web beacon, Proxy beacon, Total connection time, and DNS C2 analyses.
Minor Updates
-The malware-domains Threat Intel list is no longer available, so it has been removed from both RITA and AC-Hunter (6.2.0 and later). The change is automatic – you do not need to take any action.
-Our original release of LDAP authentication was designed to work with the Microsoft Active Directory LDAP server. As of version 6.2.0, we support Redhat’s LDAP server as well. (Many thanks to Jonathan, one of our customers, who was kind enough to help us with feedback and testing.)
-In the previous release we noted that Ubuntu 16.04 – which is no longer supported without an Extended Security Maintenance contract – would be removed as a supported operating system after 90 days. In this release we’re formally removing it from the list of supported operating systems. If you’re not using ESM on your systems we encourage you to consider upgrading to a currently supported operating system.
-Because of the Safelist application changes above, adding a safelist entry in the Beacons tab no longer offers the ability to safelist by hostname or domain. This change is only in the Beacons tab.
-Safelist comments now allow additional characters.
-The ThreatCrowd investigation source no longer appears to support searches. We’ve removed it from the investigation source menu for new installs, though it will still be listed on an upgraded system.
Bug Fixes
-Fixed a “missing funnel” display issue in Firefox
-Removed a Cross-Site Scripting issue with the User-Agent HTTP field
-Fixed a build issue related to python being upgraded to 3.10
-LDAP now accepts Distinguished Names in addition to Universal Principal Names
-docker-zeek now runs on 64bit Raspberry Pis with a 64 bit Linux operating system (aarch64)
-Additional cleanups to use “safelist”
-Fixed a build issue related to needing the full “wget” program instead of an emulated version
-merge_sensors.sh (used to create the “COMBINED” database) now correctly handles unknown files in the log tree.
-We detect and alert if docker is installed by an Ubuntu snap, a non-supported setup.
-Fixed a parsing issue with “sestatus” in newer versions of RHEL
-Removing a CIDR safelist entry no longer silently removes any IP safelist entries in that range
-The LDAPS module now supports TLS 1 through TLS 1.3
-Fixed a potential issue with snapshots not being successfully created
-LDAP queries handle timeouts more gracefully now.
-The merge_sensors.sh script now correctly handles sensors with custom names.
-Attempting to safelist an Incoming connection via Organization or ASN would fail in previous releases. This has been fixed in 6.2.0.
-The investigation menu now detects when there’s not enough screen space and adjusts its orientation.
-The “dataimport” account used to transfer Zeek files over ssh is now created as a system account.
-The bar graphs in the beacons modules will no longer disappear after safelisting an entry. This occurred occasionally due to a timing bug in previous versions.
-Zeek now installs correctly on servers running Minimal Ubuntu 18. Previously, the installer would crash due to a dependency on “tzdata” which is not installed by default.
If you have technical questions about any of the above, feel free to contact us at https://portal.activecountermeasures.com/support/ . For non-technical questions, please use this contact form.
Download AC-Hunter v6.2.0 here:
For details of how to install AC-Hunter, please see the Install Guide PDF included in the tarball or the Documentation section of this website. If you run into any issues, feel free to contact us.
Enjoy and Happy Threat Hunting!
– The Active Countermeasures Team
(For our AC-Hunter Hosted SaaS customers, we will be performing upgrades to v6.2.0 on that platform in the coming days.)
Tuesday - 04/19/2022
Version 6.1.0 of AC-Hunter Has Been Released!
AC-Hunter 6.1.0 focuses on customer requested-features. You ask, we listen!
New Features
LDAP Single Sign-on
While it’s always been possible to add multiple analyst user accounts to AC-Hunter so that each can access the web user interface, this is a manual process. 6.1.0 offers a new way to provision these using an “AC-Hunter Users” group in Active Directory.
To enable this, follow the instructions in the User Guide in the “Configuring User Accounts for the Web Interface” section.
You can continue to set up and manage accounts by hand as before if you choose not to use this new approach.
Threat Hunting in Microsoft’s Azure Cloud
We’ve had the ability to monitor cloud instances in Amazon’s EC2 environment for a few years. Since that blog was published we’ve received multiple requests to do the same thing in Microsoft’s Azure cloud.
AC-Hunter 6.1.0 provides:
A purchasable AC-Hunter appliance in the Azure Marketplace.
A setup process that enables monitoring other Azure cloud instances. We provide Azure automation runbooks for installing the Espy agent on Windows 10 Azure instances or Zeek on Ubuntu (16.04, 18.04, and 20.04) and Centos 7.x Azure instances. These agents report back to your Azure AC-Hunter instance.
For those purchasing AC-Hunter for Azure, we provide a separate Install/Setup Guide as the process is different.
Bug Fixes and Improvements
The installer now checks that your system is not in SELinux’s enforcing mode.
Typo fixed in the Safelist dialog.
Fixed permissions on AC-Hunter configuration files.
Client signatures now sort in Ascending order by default.
When merging Zeek logs from multiple sensors into a single dataset, any Zeek logs produced by Zeek or Espy running on the AC-Hunter machine are also included.
Additional Notes
Ubuntu 16.04, one of our currently supported platforms, was removed from general support a year ago (except for security fixes with an ESM support contract with Canonical). We’ll be removing this as a supported platform in 90 days. We encourage you to upgrade any remaining Ubuntu Linux 16.04 systems.
Support
Our weekly office hours – where you can sign up for a 20-minute support call with screen sharing – have been extended so that no matter where you are in the world there will be at least one time slot each week that falls in your 8am-5pm workday. Obviously, if you are 4 miles down in the Mariana Trench, we can’t guarantee your wifi will be strong enough to hold the call. 🙂
To sign up, see https://portal.activecountermeasures.com/support/support-meeting/ .
If you have technical questions about any of the above, feel free to contact us at https://portal.activecountermeasures.com/support/ . For non-technical questions, please use this contact form.
Download AC-Hunter v6.1.0 here:
For details of how to install AC-Hunter, please see the Install Guide PDF included in the tarball or the Documentation section of this website. If you run into any issues, feel free to contact us.
Enjoy and Happy Threat Hunting!
– The Active Countermeasures Team
(For our AC-Hunter Hosted SaaS customers, we will be performing upgrades to v6.1.0 on that platform in the coming days.)
Wednesday - 01/19/2022
Version 6.0.0 of AC-Hunter Has Been Released!
The Christmas lights are dark, the tree is down, and it’s freezing outside. Grab a cup of hot cocoa and enjoy a new release of AC-Hunter!
Cyber Deception
In AC-Hunter v6.0, we bring in a brand new module, Cyber Deception! This new module will allow you to create canary tokens in Windows environments for file access and user-account login monitoring to detect individuals trying to pry on your network before they access something you don’t want them to.
Any time a resource you’re monitoring via a canary token is accessed, that event will trigger an alert to AC-Hunter and be viewable within the Cyber Deception module. You can then investigate the IP address that triggered that event or even view the full Windows Event Log generated from the triggered event. We hope that this new feature will assist in detecting potential data and network breaches.
The v6.0 User Guide includes a section on how to set up canary tokens.
If you’re interested in seeing a sample data set with deception events, please open up the “dnscat-ja3-strobe” sample data set in v6.0.
Certificate Screen Removed
The process of designing and implementing RITA and AC-Hunter has been a fluid one; we’ve looked at customer needs and available data, and have tried to find good matches between the two. In most cases, these fit well together and we provide tools that help find Threats in your network.
The Certificate tab hasn’t lived up to what we, and you, need. While it’s nice to know that a certificate on a TLS or SSL server has issues, this rarely (if ever) leads to a Threat in the way that the other investigation features of AC-Hunter do. Since both RITA and AC-Hunter are primarily focused on Threat Hunting, we deprecated the AC-Hunter Certificate screen last fall and have removed it in release 6.0.0.
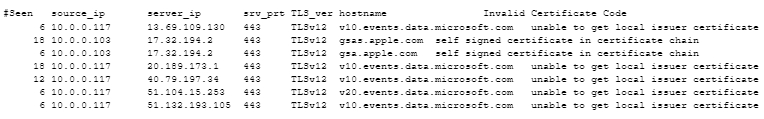
For those that have used this screen to identify certificate issues in the past, it will still be possible to locate the certificates with problems using the certificate-issues command line tool. Sample output:
#Seen source_ip server_ip srv_prt TLS_ver hostname Invalid Certificate Code 6 10.0.0.117 13.69.109.130 443 TLSv12 v10.events.data.microsoft.com unable to get local issuer certificate 18 10.0.0.103 17.32.194.2 443 TLSv12 gsas.apple.com self signed certificate in certificate chain 6 10.0.0.103 17.32.194.2 443 TLSv12 gsa.apple.com self signed certificate in certificate chain 18 10.0.0.117 20.189.173.1 443 TLSv12 v10.events.data.microsoft.com unable to get local issuer certificate 12 10.0.0.117 40.79.197.34 443 TLSv12 v10.events.data.microsoft.com unable to get local issuer certificate 6 10.0.0.117 51.104.15.253 443 TLSv12 v20.events.data.microsoft.com unable to get local issuer certificate 6 10.0.0.117 51.132.193.105 443 TLSv12 v10.events.data.microsoft.com unable to get local issuer certificate
The script is available at https://github.com/activecm/
Safelist
Starting with this release we’ll be using the term “safelist” instead of “whitelist”. These changes will be pulled in over the next few releases.
Bug Fixes and Improvements
Any searches entered in another module will be cleared when you come back to the Dashboard.
Our investigation menu for IP addresses has some new entries: Censys, Onyphe, and Symantec Site Review. If you’re doing a brand new install, these will show up by default. If you are upgrading, you can copy these new entries from /etc/AC-Hunter/config.yaml.
Previous releases ran into a “missing tool” problem when the install was started on a Mac and the install command line used hostnames. This has been resolved.
The distributed tar file includes a “Where do I start?” document in both text and PDF formats, covering where to find resources to get going with AC-Hunter.
We resolved an issue where logs were not being imported when the sensor had a custom name.
When a data set contains more than 24 hours worth of data (due to long connections longer than 24 hours, for example), we now display the most recent 24 hours where the most interesting data can be found.
As always, there are lots of other behind-the-scenes changes and tweaks to AC-Hunter.
Special Thanks
We’d like to extend our thanks to the individuals who were willing to Beta test this release.
Support
Over the past few months we’ve upgraded our email support system in multiple ways. We’re doing a better job of tracking issues so that nothing falls through the cracks. You get to rate your support and (optionally) add a comment so we know where to improve it.
We’ve also added other support options. When we have staff available – mostly covering US time zones – we have a live support chat available. Go to any password protected page here (such as https://portal.
Download AC-Hunter v6.0.0 here:
https://portal.
For details of how to install AC-Hunter, please see the Install Guide PDF included in the tarball or the Documentation section of this website. If you run into any issues, feel free to contact us.
Enjoy and Happy Threat Hunting!
– The Active Countermeasures Team
(For our AC-Hunter Hosted SaaS customers, we will be performing upgrades to v6.0.0 on that platform in the coming days.)
Wednesday - 12/15/2021
New log4j Advisory
MITRE and the Apache Software Foundation (log4j’s authors) have put out a second advisory (CVE-2021-45046) as an addendum to the original (CVE-2021-44228). These advisories point to a weakness in a software package called log4j that is used behind the scenes in our BeaKer software.
The new advisory points out that the workaround we mention below under “BeaKer Workaround” will not handle all the potential ways this vulnerability could be exploited, and they recommend removing a Java library entirely. Even though the text of CVE-2021-45046 says that this can only be exploited in certain circumstances, and even then, the result is limited to a denial of service, we feel this is worth fixing in the short term.
We’re putting out an interim release of AC-Hunter (5.4.1) that only removes this library and has no other changes. Based on the 2 advisories above we feel that this one change will address both log4j advisories completely. We’re also confident that this sole change will not have any negative effects on BeaKer’s or AC-Hunter’s functionality.
If you are not using BeaKer, you do not need to upgrade to 5.4.1.
If you are running BeaKer, please download AC-Hunter version 5.4.1 from your account here. Perform the upgrade as normal, making sure you upgrade BeaKer.
(optional step) To confirm that this library has been removed, run the following two commands after the upgrade is complete:
sudo docker cp beaker_elasticsearch_1:/usr/share/elasticsearch/lib/elasticsearch-log4j-7.16.1.jar /tmp/5.4.1-elasticsearch-log4j-7.16.1.jar unzip -l /tmp/5.4.1-elasticsearch-log4j-7.16.1.jar | grep -i jndilookup || echo jndilookup removed.
With the library gone you should get this output back on the next line:
jndilookup removed.
If you run into any issues with the upgrade, please contact us by one of the methods on https://portal.activecountermeasures.com/support/ .
We’ll continue to monitor for new information coming out about this and will keep you posted if additional steps are needed in the future.
Note: the original text below (dated Monday – 12/13/2021) suggested a series of commands that would mitigate this vulnerability. Based on new information, if you are a BeaKer user, we strongly recommend that you instead upgrade to AC-Hunter version 5.4.1 , which contains a more complete fix to the issue.
Additional Questions
If you have other questions not answered by this note, please feel free to contact us using any of the methods found here.
– The Active Countermeasures Team
Monday - 12/13/2021
Handling the log4j Issue
We’ve been looking into how any of our tools use log4j:
(Overall coverage of the issue: https://nvd.nist.gov/vuln/detail/CVE-2021-44228 )
Our own code does not use log4j.
- Specifically, AC-Hunter, Espy, Kibana, passer, pcap_stats, RITA, Winlogbeats, and Zeek do not have the recent issue reported with log4j.
- A supporting package for BeaKer (Elasticsearch) does use it.
- If you do not use BeaKer, you do not need to take any actions and can stop reading here.
- If you are an AIHHosted customer, the workaround listed below has already been applied to your AIHHosted instance; you do not need to take any action to mitigate this.
BeaKer
Details
(Details come from the elastic.co link in References.)
Elasticsearch is not susceptible to remote code execution from this vulnerability. However, Elasticsearch is potentially vulnerable to an information leak (which does not permit access to Elasticsearch data) when running on JDK 8 or below.
AC-Hunter 6.0.0 will include a permanent fix for the issue. Until that is released, we encourage you to use the workaround below.
BeaKer Workaround
First, confirm that you have BeaKer running at all by running:
sudo docker ps | grep -i activecm-beaker/elasticsearch
If this output includes lines with
... activecm-beaker/elasticsearch ...
then you are running BeaKer on this system. If this above command has no output, you are not running BeaKer on this system.
To patch the system against this issue, run
beaker down
Next, edit the following file with your favorite editor under sudo:
sudo nano /opt/BeaKer/docker-compose.yml
In that file, look in in services>environment and change the existing line:
- "ES_JAVA_OPTS=-Xms3g -Xmx3g"
to
- "ES_JAVA_OPTS=-Xms3g -Xmx3g -Dlog4j2.formatMsgNoLookups=true"
Please be careful to leave the spaces at the beginning of that line (on the systems we’ve installed there were 6 spaces before the dash) just as they are; the indentation is important. If you are copying the line from this advisory, please make sure both double quotes are standard double quotes and not ‘smart quotes’.
Save the file and exit. Finally, run:
beaker up -d
We do not believe that this will have any negative effect on your use of BeaKer.
For more details on the above workaround, see:
https://www.elastic.co/guide/en/elasticsearch/reference/7.16/advanced-configuration.html#set-jvm-options
Beaker Fixed Release
We intend to make a new AC-Hunter release with fixed code for Beaker. Until this is available, we strongly encourage you to apply the above workaround.
References
Overall coverage of the issue: https://nvd.nist.gov/vuln/detail/CVE-2021-44228
What is/isn’t vulnerable from the Elasticsearch suite:
https://discuss.elastic.co/t/apache-log4j2-remote-code-execution-rce-vulnerability-cve-2021-44228-esa-2021-31/291476
Side Note
Our ipfix-rita project, which only worked with Version 2 of RITA and is no longer supported, may have a vulnerability with the Logstash code included in it. We do not recommend you use this package. This is different from the Active-Flow module in AC-Hunter (which is not vulnerable to this issue).
Additional Questions
If you have other questions not answered by this note, please feel free to contact us using any of the methods found here.
– The Active Countermeasures Team
Friday - 09/17/2021
Certificate Screen Being Deprecated
The process of designing and implementing RITA and AC-Hunter has been a fluid one; we’ve looked at customer needs and available data, and have tried to find good matches between the two. In most cases these fit well together and we provide tools that help find Threats in your network.
The Certificate tab hasn’t lived up to what we, and you, need. While it’s nice to know that a certificate on a TLS or SSL server has issues, this rarely (if ever) leads to a Threat in the way that the other investigation features of AC-Hunter do. Since both RITA and AC-Hunter are primarily focused on Threat Hunting, we’ve decided to deprecate the Certificate screen in AC-Hunter and intend to remove it in a release later this year (no sooner than November).
For those that have used this screen to identify certificate issues in the past, it will still be possible to locate the certificates with problems using a command line script that we’ll provide with AC-Hunter. Sample output:
If you have any questions or comments about this, please reach out to us.
– The Active Countermeasures Team
Thursday - 09/09/2021
Version 5.4.0 of AC-Hunter Has Been Released!
“…buckle your seatbelt, Dorothy, ’cause Kansas is going bye-bye.”
–Cypher, The Matrix
The big change to 5.4.0 is import speed. We know that the speed with which Zeek logs can be pulled into AC-Hunter has a direct impact on how fast a network we can monitor (1 hour logs for high speed networks could, in some cases, take more than an hour to import!)
Our developers took on the task of identifying import bottlenecks. In the process they removed some queries that didn’t need to happen, created some database indexes that sped up other queries, and changed the structure of how the import happened. In our testing the import runs between twice as fast and 4.5 times as fast – a 100% to 350% improvement in speed!
The end results are that AC-Hunter should be able to monitor more heavily loaded networks and it will take less time to present the new data to you each hour.
Additional Improvements in This Release
- Whitelist processing will be faster. In our testing, we found a 100%-200% improvement in speed in most cases. Speed increases will depend upon individual datasets and whitelist entries.
- Improved pagination and scrolling for some modules. This allows for faster loading of some pages.
- Fine-grained control over dataset analysis. You can define a list of specific sensors that will be analyzed, which comes in handy when you have multiple sensors and merge them all into a COMBINED sensor. Restricting analysis to specific individual datasets can result in a performance improvement. For more details, see the “Only importing specific sensors” section of the User Guide.
- The default number of connections for the communication between two IP addresses to be considered a strobe has been lowered to 1 connection per second.
- An option has been added to the RITA configuration file which filters out connections from external hosts to internal hosts when enabled. See “Ignoring incoming traffic” in the Install Guide for more details.
Bug Fixes
- When whitelisting the final beacon for an IP address, the score for that IP address on the dashboard wasn’t being updated. This is fixed in 5.4.0 .
- Proxy beacon analysis now looks at the last 24 hours of data rather than just the current hour.
- FQDN beacon analysis now looks at the last 24 hours of DNS logs rather than just the current hour.
- Adding a wildcard domain entry (e.g., *.microsoft.com) to the whitelist will result in dashboard scores for proxy beacons and FQDN beacons being properly updated.
- Removing entries from the whitelist will result in dashboard scores for proxy beacons and FQDN beacons being properly updated.
- Syslog alerts were not being sent when the scoring breakdown was enabled. This has been fixed.
- We fixed some obscure bugs in the installer.
- Whitelists will automatically be applied to rolling snapshots and manually-imported data rather than on the first time that these datasets are visited.
- Existing whitelists are applied to sample data during the installation process.
- All filter criteria now work properly in the dialog for viewing/searching whitelist entries
- Various bug fixes in the user interface.
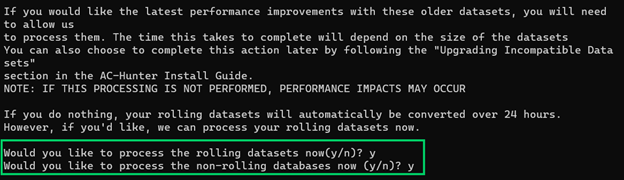
When you are picking a dataset you may see a note below the database name that says “This database is currently being filtered.” In the background, AC-Hunter is applying whitelist entries to the database. You’re still welcome to select it and work with it just like any other database, but be aware that recent whitelist changes may not have been applied yet (you may see records that should have been filtered by a recent whitelist addition, or you may not see records that should come back to view after a recent whitelist removal).
The warning note may show up in multiple places:


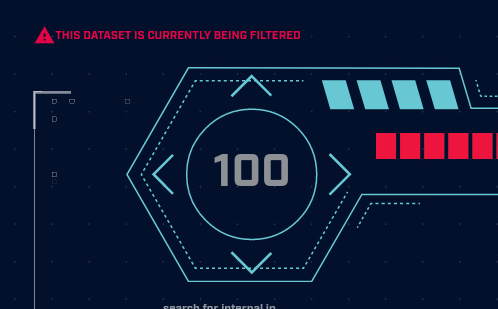
If you are upgrading from version 5.3.0 or 5.3.1 of AC-Hunter, you will be prompted to allow AC-Hunter to perform processing on your existing datasets. This processing is needed to ensure that your system can take advantage of the latest performance improvements for adding whitelist entries and importing whitelist files. WE HIGHLY RECOMMEND THAT YOU ALLOW AC-HUNTER TO PERFORM THE PROCESSING. If you do not allow AC-Hunter to perform the processing on the existing datasets, it is possible that you will see a decrease in performance for whitelisting.
This processing does not require that AC-Hunter perform a re-import and re-analysis of your datasets, which means that it should be much faster than re-importing the data. The length of time this will take will vary depending on the size and number of your datasets. If you are upgrading from a version of AC-Hunter prior to version 5.3.0, you will likely be prompted to allow AC-Hunter to re-analyze your data, which could be a lengthier process depending on the size and number of your datasets.
Conclusion
As a final note, we’ve also updated the default whitelist with additional domains that are commonly used. The whitelist can be found at https://portal.activecountermeasures.com/whitelist/ , and more details about these additions are in the updated whitelist announcement on this page below.
The most recent version of AC-Hunter can be found at https://portal.activecountermeasures.com/my-account/downloads
As always, this new release includes additional behind-the-scenes improvements to make it more stable and efficient.
For details on how to install it, please see the Install Guide PDF included in the tarball or the Documentation section of this website. If you run into any issues, feel free to contact us.
Enjoy and Happy Threat Hunting!
– The Active Countermeasures Team
(For our AC-Hunter Hosted SaaS customers, we will be performing upgrades to v5.4.0 on that platform in the coming days.)
Tuesday - 07/27/2021
Version 5.3.1 of AC-Hunter Has Been Released!
5.3.1 is primarily a bug fix release. Here’s how to decide if you need to upgrade to it or not:
If you did not upgrade to 5.3.0:
We encourage you to skip 5.3.0 and upgrade to 5.3.1. There are a number of significant performance and functionality improvements in 5.3.0 (that are also in 5.3.1, obviously).
If you did upgrade to 5.3.0 and had no problems with the upgrade:
This upgrade is optional for you. The only bug fixes not related to the install is a fix to the tooltip for the Long Connections port/protocol/service and a fix to allow Proxy Beacons analysis to work without additional AC-Hunter configuration. If these are not an issue for you, you can skip this upgrade.
If you did upgrade to 5.3.0 and had problems with the upgrade:
We encourage you to upgrade to 5.3.1 . We’ve fixed some issues in the upgrade process.
Bug Fixes and Improvements
- Fix bug where the whitelist collection wasn’t being renamed for some users
- Fix bug where data transfer ssh keys were not transferred if target user did not have a `~/.ssh` directory
- Fix bug where AC Hunter had to be running in order to perform a successful upgrade
- Fix overflow and add tooltip for the port protocol service list in the long connections module
Finally, we have updated the User Guide to provide more context to the Proxy Beacons analysis first introduced in 5.3.0 .
Conclusion
The most recent version of AC-Hunter is available to download now: https://portal.activecountermeasures.com/my-account/downloads
As always, this new release includes additional behind-the-scenes improvements to make it more stable and efficient.
For details on how to install it, please see the Install Guide PDF included in the tarball or the Documentation section of this website. If you run into any issues, feel free to contact us.
Enjoy and Happy Threat Hunting!
– The Active Countermeasures Team
(For our AC-Hunter Hosted SaaS customers, we will be performing upgrades to v5.3.1 on that platform in the coming days.)
Thursday - 07/15/2021
A New Version of the AC-Hunter Default Whitelist Has Been Released
The default whitelist for AC-Hunter is provided to give you a head-start of building or adding to your own custom whitelist. Included in the default whitelist are commonly known traffic destinations to resources such as; root nameservers, OS and application patch/update servers and NTP servers.
We have a new version of the Default Whitelist available for you. This new list includes some new domains (below) and removes one domain from the previous Default Whitelist (“storage.googleapis.com”) as we believe it has potential to hold untrustworthy content. We encourage you to remove it from your whitelist.
To use this new one, download the file and unzip it with:
unzip ac-hunter-default-whitelist.202107151318.zip
Now go to your AC-Hunter console, click on “Dashboard”, then the gear icon in the upper right, then “Whitelist” and press “Upload Whitelist”. Find the ‘ac-hunter-default-whitelist.202107151318.json’ file and press “Upload”. These new entries will be merged with your existing whitelist and deduplicated.
#Additions:
*.conferdeploy.net *.cymru.com *.events.data.microsoft.com *.microsoft.com *.msidentity.com *.paloaltonetworks.com *.r7ops.com *.rapid7.com *.sophos.com *.sophosxl.net *.spamcop.net *.spamhaus.org *.symantec.com *.trafficmanager.net *.windows.net autopush.prod.mozaws.net cloud.tenable.com detectportal.firefox.com location.services.mozilla.com login.live.com login.microsoftonline.com mtalk.google.com ntp.barracudacentral.com ocsp.comodoca.com ocsp.sectigo.com push.services.mozilla.com
Access and download the new default whitelist file here.
Enjoy and Happy Threat Hunting!
– The Active Countermeasures Team
Wednesday - 07/07/2021
Version 5.3 of AC-Hunter Has Been Released!
There’s nothing quite like the smell of a bakery, especially when the baker opens the oven and brings out a tray of fresh-baked AC-Hunter releases. 🙂 We give a tip of the hat to the world’s best development team for preparing version 5.3.0 for you.
New Features
Proxy Beacons
Version 5.3.0 now includes the ability to look for beacons that are sent through an HTTP proxy. At sites that use an HTTP proxy, we can now look for beacons and report them on the Proxy Beacons and BeaconsFQDN tabs just like we do for beacons identified from network traffic.
You will need a Zeek sensor placed in front of the HTTP proxy. As you might expect, this can report on HTTP proxy traffic but not HTTPS proxy traffic.
Whitelist
We now include the ability to search the whitelist – useful if you have a lot of entries in it.
Now that you can whitelist beacons by fully qualified domain name, we have a new default whitelist available! It’ll be far more efficient than the previous one was. For details on upgrading, please see our blog post, “Upgrading to the new default whitelist“.
IP Address Details
When AC-Hunter is able to display the location of an IP address, it used to display just the City. We now include the State when one is available. We also show the “comm” field (which includes the port, protocol, and service) whether the IP address is public or private.
Open Connections
Zeek, by default, doesn’t show connections until they close. Connections that stay open for weeks or months may never show up in the output.
We now display open connections, allowing you to see these long term ones as well. To enable this you’ll need to reinstall Zeek to your sensor as part of installing AC-Hunter. If you don’t upgrade Zeek, you won’t get the new open connections feature.
Dashboard
You can now search for a specific IP address in the Dashboard Hosts list.
New Utilities
We include a new script that will create a database from a pcap file, import_pcaps.sh . To use it, run:
/usr/local/bin/import_pcaps.sh -p /full/path/to/pcap_filename.pcap -d new_database_name
We also have a tool that will create multiple web UI user accounts at once. See the notes at the top of ‘/usr/local/bin/bulk_add_users.sh’ for details.
Bug Fixes and Improvements
Alerting
We found a bug introduced in the 5.1.0 release that blocked both syslog and Slack alerts from being sent. The bug has been fixed, so this release will be able to generate both types of alerts again. Once 5.3.0 is installed the alerts will start flowing again – you do not need to take any additional action. We apologize for the broken feature.
Importing/BeaconFQDN
In version 5.2.0 on heavily loaded networks the import process could take an undesirably long time; importing an hour’s worth of data could take longer than an hour. The import code (also part of the open-source RITA project) has been updated in RITA 4.3.0 and AC-Hunter 5.3.0 to process the data more efficiently.
If you had to disable BeaconFQDN processing as a workaround in 5.2.0, you should be able to re-enable that in 5.3.0. We’d love to hear if this one change is sufficient to get BeaconFQDN processing working for you again or not.
Scoring
Now that AC-Hunter has three methods of Beacon analysis (by IP address, by Fully Qualified Domain Name, and for traffic through a HTTP proxy), the total threat score receives twice as much influence from beacon traffic as it should. In 5.3.0 only the larger of the scores is used in the total threat score.
We’ve also introduced optional caps on the individual scores; if you find that one threat type is dominating the total score, you can configure a maximum score cap for that type. See the User Guide for an example (“Setting Maximums for the Threat Activity Scores”).
New Version Check
AC-Hunter will let you know when a new version is available by presenting a banner in the UI.
Certificates
In AC-Hunter versions 5.2.0 and below there was a bug that prevented Invalid Certificate errors from being removed correctly from rolling databases. AC-Hunter 5.3.0 (and RITA 4.3.0) include a fix that correctly removes these from rolling databases.
In both the Certificate and User Agent tabs there may have been times where an entry showed up in multiple places because of a sort issue. That’s now been resolved.
Whitelist
Whitelist modifications are now processed in the background, allowing you to continue working with AC-Hunter while the changes are being applied to all of your existing databases.
In certain circumstances, previous versions of AC-Hunter would fail to apply these changes to all databases if AC-Hunter or the system on which it was running was shut down. 5.3.0 fixes this by having a queue of changes to apply which is restarted when AC-Hunter is restarted.
Ubuntu
We’ve raised Ubuntu 20.04 to fully supported. As always, please let us know if you run across install or operation issues with any supported operating system.
MongoDB
MongoDB has been the database shipped with AC-Hunter. AC-Hunter v5.3.0 uses MongoDB v4.2.0 since previous versions have reached end of life. For upgrade installs, your MongoDB instance will be upgraded. Your previous datasets will be backed up to /opt/AC-Hunter/mongo_backups during the install. These can be reimported into MongoDB in the case that something goes awry.
We hope that the fixes and features in 5.3.0 help you do your work more efficiently. If you had any performance issues with 5.2.0 or below we strongly encourage you to upgrade when possible. If these issues were severe enough that you had to disable BeaconFQDN processing, we ask you to leave this off for a day or two to make sure all is working well, then consider re-enabling BeaconFQDN processing (*).
The most recent version of AC-Hunter can be found at https://portal.activecountermeasures.com/my-account/downloads/ . If you’re upgrading from a previous version, please make sure AC-Hunter is running while doing the installation (i.e., don’t shut it down with the hunt command.
* Edit /etc/AI-Hunter/rita.yaml with:
sudo nano /etc/AI-Hunter/rita.yaml
and change the existing:
BeaconFQDN: Enabled: false
To
BeaconFQDN: Enabled: true
Save and exit, and restart AC-Hunter with:
hunt up -d --force-recreate
Conclusion
As always, this new release includes additional behind-the-scenes improvements to make it more stable and efficient.
For details on how to install it, please see the Install Guide PDF included in the tarball or the Documentation section of the portal website. If you run into any issues, feel free to contact us.
Enjoy and Happy Threat Hunting!
– The Active Countermeasures Team
(For our AC-Hunter Hosted SaaS customers, we will be performing upgrades to v5.3.0 on that platform in the coming days.)
Friday - 05/07/2021
A New Version of the AC-Hunter Default Whitelist Has Been Released
The default whitelist for AC-Hunter is provided to give you a head-start of building or adding to your own custom whitelist. Included in the default whitelist are commonly known traffic destinations to resources such as; root nameservers, OS patch/update servers and NTP servers.
Access to the default whitelist file here has changed from My Account/Downloads to a dedicated page on the Main Menu under Support/Whitelist.
Enjoy and Happy Threat Hunting!
– The Active Countermeasures Team
Thursday - 04/22/2021
Version 5.2 of AC-Hunter Has Been Released!
AC-Hunter 5.2.0 is being released primarily to provide a fix to a current performance issue.
Fix
Whitelisting Performance
Short version: AC-Hunter 5.2.0 will be much faster at adding or removing whitelist entries.
Long version: AC-Hunter 5.1.0 and below applied whitelist changes to all databases before returning the user interface back to you. 5.2.0 applies the whitelist addition or removal to the currently selected database and returns the user interface back to you, and queues up the changes to the other databases to happen in the background.
We’ve also put some time into speeding up the task of applying a single change to a single database, so the system should be orders of magnitude faster at applying changes.
Known Issues With This Release
1. There’s a known problem in 5.2.0 that shows up when deleting a whitelist entry and restarting AC-Hunter soon after. If you ask to delete a whitelist entry and reboot the system, restart AC-Hunter, or install a new version of AC-Hunter (such as 5.3.0) before the deletion has been completely applied to all databases, the deletion will not continue after AC-Hunter restarts.
If it becomes necessary to restart AC-hunter for any reason, we encourage you to run “top” first on the system to see when the AC-Hunter docker containers and Mongo database slow to idle first and reboot after that.
Note; this problem does not show up when adding a whitelist entry; this queued task will continue after rebooting.
2. If your drop-down investigation menu (on an ip address) includes the web site apility.io, that web service no longer exists. If you click on that you’ll get an error that the site no longer resolves. We’ll remove that in the next release. This is only a cosmetic issue.
Workaround: If you’d prefer to remove that now, you can run the following 2 commands on the AC-Hunter system to remove it from the investigation menu. The first command is likely wrapped – everything from “sudo sed” to “/etc/AI-Hunter/config.yaml” is one command. Both of the quotes are single quotes (under double quotes on the keyboard).
sudo sed -i.withapility 's/^\([[:space:]]*\)apility\.io/\1#Service dead. apility.io/' /etc/AI-Hunter/config.yaml
hunt up -d --force-recreate
Conclusion
As always, this new release includes additional behind-the-scenes improvements to make it more stable and efficient.
This newest version of AC-Hunter is available for download now: https://portal.activecountermeasures.com/my-account/ (under Downloads)
For details on how to install it, please see the Install Guide PDF included in the tarball or the Documentation section of this website. If you run into any issues, feel free to contact us!
Enjoy and Happy Threat Hunting!
– The Active Countermeasures Team
Wednesday - 03/17/2021
Version 5.1 of AC-Hunter Has Been Released!
New Features
Beacon Detection and Whitelisting by Domain Name
The big news in version 5.1.0 is whitelisting by domain name. To explain why, we need to give a little background (don’t worry, this will be brief).
As security professionals we know that a tool that constantly presents benign information to human eyes will not be used for long – one of the reasons why we find log analysis so tiring.
To avoid this AC-Hunter has steadily added new ways to whitelist:
– By source or destination IP
– By IP, ASN, ASN organization, or subnet
– By pairs of IP addresses
These tools get benign traffic off the screen, but they don’t address the question: What do we trust?
Ideally we want to assign trust in a company or organization, which often maps neatly to a domain name. If I state that I want to put trust in the public network of time servers that show up on the beacon screen all the time, now I can whitelist “*.pool.ntp.org.”. That one whitelist entry replaces about 3,600 IP addresses for the entire pool. If I run Ubuntu Linux and want to trust the patch servers and other systems that support those, I can whitelist “*.ubuntu.com.”
Not only does the size of the whitelist shrink dramatically, but you also get to clear off benign traffic more quickly and more accurately. There’s far less chance of trusting an IP at a Cloud provider and never realizing that the IP you whitelisted was later assigned to a different – and far less trustworthy – client.
On a practical note, the AC-Hunter interface now has 2 Beacons tabs. The new one considers connections between your client IPs and external host names. The old one shows connections between internal and external IP addresses (identical to the Beacons tab you’ve worked with before).
As always, we discourage any whitelisting strategy that ends up whitelisting large blocks of cloud services (like “*.amazonaws.com.”) since you’re not placing trust in the cloud provider. Instead, whitelist the domain names your clients look up.
Bug Fixes and Improvements
Whitelist Pairs Are Now Unidirectional
We have one security improvement to whitelisted pairs of IPs. When you entered a pair of addresses (say 1.1.1.1 and 8.8.8.8), earlier releases would allow connections in both directions: from 1.1.1.1 to 8.8.8.8 and from 8.8.8.8 to 1.1.1.1 .
Since these pairs usually are intended for traffic in one direction we decided to return this to unidirectional whitelisting (just from 1.1.1.1 to 8.8.8.8). If you need to allow connections in the other direction, you can add a second whitelisted IP pair (in the above example: 8.8.8.8 to 1.1.1.1).
Ubuntu 20.04 Installer Fix
While Ubuntu 20.04 LTS is not a fully tested platform, we have enough customers using it now to include it in our Beta support program. Please feel free to give it a try and let us know if you find any issues!
The installer in 5.1.0 includes a fix to a packaging bug that affected Ubuntu 20.04; the install should now proceed successfully. We’ve also cleaned up the installer to more gracefully handle other packaging corner cases.
Unfortunately we did have one more bug that showed up late in testing. Before you start the install, run the following command on all systems to work around it:
sudo apt-key adv --keyserver hkp://keyserver.ubuntu.com:80 --recv-keys 656408E390CFB1F5
Additionally
- We check that Docker’s network blocks aren’t in use before trying the install.
- Since a single system can’t run more than one of Zeek, Espy, and Active-Flow, we block that in the installer.
- On the dashboard, instead of showing “>100” Threat Score, we show the actual number.
- In some circumstances we hid the error messages coming out of the tool that patches the system and installs new packages. Now we show those, making it much easier to identify and fix packaging issues. The side effect is that you’ll see more status messages from these tools.
- The IP address information block at the top center of the Beacons, Strobes, and Long connections screens use to provide a long list of all hostnames we’ve found for this IP address (in the field “fqdn”). Starting in 5.1.0 we show the specific name this host requested in the “queried fqdn” field, and all other names we have for this host in the “historic fqdn” field.
- The Dashboard used to refer to “TXT Query Count” * as one of the components of the combined threat score. For detecting c2 over DNS, it is more useful to know how many unique FQDNs have been queried by a particular host, so this field has been updated to reflect this count. It has been relabeled to “Too Many FQDNs Per Domain.”
- In our August 2020 4.0.0 release we mentioned that apility.io was deprecated as an investigation source as it had been acquired by Auth0. It was removed in 5.1.0. If you use this service and have an account there, there’s a line that can be uncommented to enable Auth0 (see “Customizing Investigation Sources” in the User Guide).
Known Issues
Independent of the whitelist-by-domain feature above, we’re aware of a slowdown in adding and removing whitelist entries. We’re investigating it and hope to have an answer for it soon.
Coming Soon
Default Whitelist Improvements
We’ll be updating the Default whitelist to use the new whitelist-by-domain-name feature. When ready you’ll find the updated list in the Portal under Downloads.
Conclusion
As always, this new release includes additional behind-the-scenes improvements to make it more stable and efficient.
This newest version of AC-Hunter is available for download now: https://portal.activecountermeasures.com/my-account/ (under Downloads)
For details on how to install it, please see the Install Guide PDF included in the tarball or the Documentation section of this website. If you run into any issues, feel free to contact us!
Enjoy and Happy Threat Hunting!
– The Active Countermeasures Team
Thursday - 01/14/2021
AC-Hunter Version 5.0.1 Is Provided to Address an Issue in 5.0.0 Related to Upgrading the Whitelist
This issue only shows up on upgrades (not on fresh installs) and only on some systems that have whitelist entries.
We encourage you to upgrade to 5.0.1 if you have entries in or plan to add entries to your AC-Hunter whitelist.
You should be aware that all upgrade approaches to the 5.0 series (both 5.0.0 and 5.0.1) run some risk of losing misformatted whitelist entries. For that reason we encourage you to make a backup of your whitelist before trying any upgrade. If any whitelist entries are lost during the upgrade and you end up re-entering them you’ll have the old whitelist file for reference.
Tuesday - 01/12/2021
Version 5.0 of AC-Hunter Has Been Released!
There’s nothing quite as peaceful as a light snowfall outside, a lovely fire to keep us warm, and software release notes to kindle the true spirit of the new year. 🙂
Our developers have been working tirelessly to bring you AC-Hunter(*) 5.0.0 . Here are the highlights from this release:
Spotlight Feature
Espy
One of our most-requested features relates to the fact that so many people are working from home. Unlike an office with a network that can be easily monitored by Zeek, we now have hundreds of single-employee homes, making it impractical to set up Zeek sensors at all of them.
We’d like to introduce Espy. Espy is an agent that runs on the employees’ Windows machines. In a manner similar to how BeaKer collects forensic information on network connections, Espy provides the information AC-Hunter needs to perform Threat Hunting with no network sensor! This means that we can monitor for Threats on individual workstations without having to provide all the hardware to run Zeek at every home.
Espy is open-source so you can use it with or without AC-Hunter. It’s also considered to be beta-level; it’s likely we’ll have improvements to it over the next few months.
Upgrading to 5.0 will automatically upgrade recent databases to support the Espy database requirements.
Improvements and Bug Fixes
To save memory, Zeek used to forget connections if they sat idle for more than 5 minutes. It had the side effect that a single actual connection could appear to be tens of connections, filling up the display. We’ve changed the default timeout to 60 minutes to clean up the display and reduce the number of connections to consider.
We had a bug that showed up if one attempted to import a range of IP addresses from a json whitelist file. This only showed up if one attempted to manually edit the whitelist file. It has now been fixed.
AC-Hunter includes the new release of RITA, 4.0. This supports faster data import, has new Threat Intel Feeds to reduce false positives, and supports Espy by allowing logs to combine multiple sysmon feeds. It also removes two lower quality Threat Intel Feeds. This means you should see less noise in your Threat Intel screen.
The timeline connection chart at the bottom of the beacons and threat intel page now shows times in the browser’s local timezone rather than UTC.
Upgrade Notes
Databases created under earlier versions will need to be converted during the AC-Hunter upgrade. The installer will offer to upgrade the most recent 7 days of databases automatically.
The whitelist format has been updated. During the install, the currently active whitelist will be automatically updated. You’ll want to export the whitelist after the upgrade. If you have any saved whitelist files you wish to later import these will need to be manually converted. We’ll have a FAQ entry soon for how to do this at https://portal.activecountermeasures.com/support/faq/.
Errata:
The Active-Flow, Zeek, and Espy packages need to run on separate machines if you’re using more than one of them. The install script does not currently block you from installing them on the same machine, though this check will be added in the next release.
As always, the new release includes additional behind-the-scenes improvements to make it more stable.
We hope you enjoy it and had a good holiday break!
– The ACM Elves
This newest version of AC-Hunter is available for download now in your account. (under Downloads)
For details on how to install it, please see the Install Guide PDF included in the tarball or the Documentation section of the portal website. If you run into any issues, feel free to contact us: [email protected]
* If you haven’t already seen the blog about the name change: https://www.activecountermeasures.com/introducing-ac-hunter/
Thursday - 08/20/2020
Version 4.0 of AI-Hunter Has Been Released!
This release was packed with a lot of improvements behind the scenes, but we still have some goodies to be excited for.
New Features:
More Investigation Menus!
We now support investigation menus for ASN’s, FQDN’s, JA3 hashes, and UserAgent strings. These menus can be found in many more places , and we hope that these new menu types will aid you in your threat hunting adventures. All of these new menu types support the “copy to clipboard” functionality released in v.3.8.
We also now have dropdowns for multiple addresses! If you have a row of multiple sources, requests, or domains, each source in that row has its own submenu, allowing you to hunt each individual address.

There’s also an IP investigation menu for the CONN– IP in deepdive!
New Threat Intel View!
In previous versions, Threat Intel view 1 displayed outbound threats and Threat Intel view 2 displayed inbound threats. These two separate views have now been combined into a single view. The new view displays both inbound and outbound threat intel IP connections.
There’s a new column with an icon that indicates whether the threat connection is inbound or outbound. Notice that the first IP in the table (orange) is an outbound connection, as the arrow is pointing away from the internal IP and out towards the internet. The last IP in the table (blue) is an inbound connection, as the arrow is pointing from the internet towards the internal IP. If an internal IP has both inbound and outbound connections, each connection will display in it’s own row (as shown above) since each connection can have different connection counts, bytes transferred, and comm ports.
More Items in Tables per Page!
Depending on your screen size, the tables across modules will display more items per page, reducing the number of pages you’ll need to flip through.
Installer Now Has a Capture Interface Selection Prompt
There’s now a much nicer selection prompt for choosing which capture interfaces you want Zeek to listen to, including interface recommendation to help clear up any confusion and avoid breaking the install.
Added Auth0 Signals as Disabled Investigation Source
Apility.io has been acquired by Auth0 and will eventually be taken down. It will be replaced with Auth0 Signals. We’ve preemptively added Auth0 Signals as a disabled source in case you’ve decided to move over to their new platform.
Potentially Breaking Changes:
- Disabled external Mongo listening port as it doesn’t need to be seen by the outside world.
- Disabled TLSv1 & TLSv1.1 as these are considered insecure. Since all modern browsers support TLS v1.2 and above, this should have no effect on accessing AI-Hunter.
- Default web account credentials no longer stored in env file
- Install in /opt/AI-Hunter and link scripts in /usr/local/bin so that utilities will be accessible from anywhere.
- Cleanup deprecated scripts
- Removed `delete-databases.sh`
- Removed `rita-import.sh`
- `install_bro.sh` no longer uninstalls RITA on upgrade
- Convert AI-Hunter to use Zeek, replacing the older “Bro”.
- Install Zeek init script
- Removed helpers directory
Bug Fixes:
- Upgrade prompt in installer will only prompt for recent datasets
- BeakerHost entry in YAML config will not be duplicated if it already exists
- Fix bug where Beaker was inaccessible from UI if host had an IPv6 address.
- Fixed sorting in strobes
- Fixed miscellaneous sorting issues
- Fixed bug where dns threshold wasn’t cleared when visiting another page
This newest version of AI-Hunter is available for download now.
For details on how to install it, please see the Install Guide PDF included in the tarball or the Documentation section of the portal website. If you run into any issues, please reach out to us for help.
Enjoy and Happy Threat Hunting!
– The Active Countermeasures Team
Thursday - 05/21/2020
Known AI-Hunter/BeaKer Bug in 3.8.0 and Above
The Beaker icon in AI-Hunter may not perform any action. If you click on it and it does not open up a new tab with the BeaKer Search page and the BeaKer server has an IPv6 address, see the FAQ entry here.
Tuesday - 05/05/2020
New Version of AI-Hunter Released!
AI-Hunter version 3.8.0 offers:
- The ability to identify what program created a connection
- Submenus for Investigation sources
- The ability to ingest Netflow V9 data from routers and switches
Once a potential threat is found, the next step is figuring out whether the activity is malicious or benign. That commonly includes getting access to the local system, looking at what programs are running, and seeing if you can match up the threat to the running programs. If that program isn’t currently running it’s usually too late to do this.
In response to this, we’ve added a new feature that helps you match up the network traffic to the program that created it! With BeaKer, your Windows systems regularly report on the running programs and what network connections they spawn. The BeaKer server remembers these, so if you need to come back even weeks later and ask “What program was responsible for this connection?”, BeaKer will give you this. While looking at a connection, click on the new “beaker” icon on the beacons page to see what Windows program triggered the traffic.
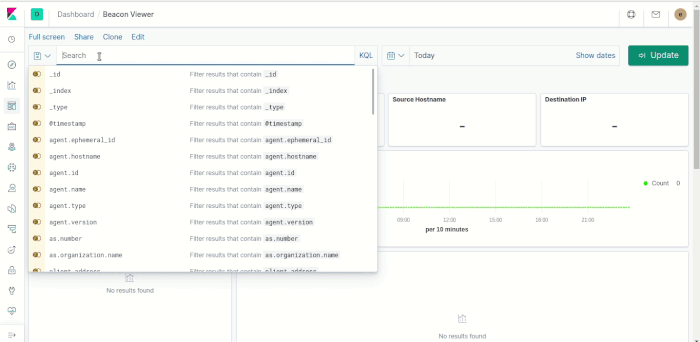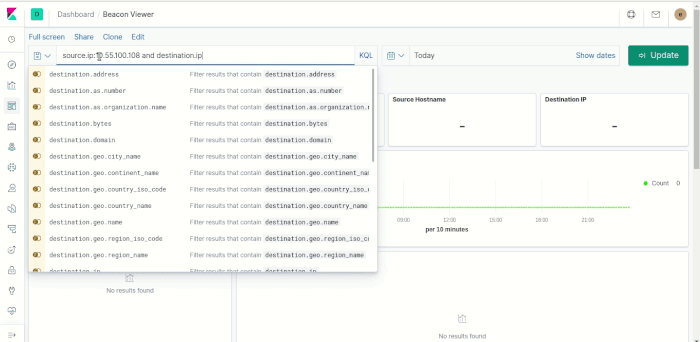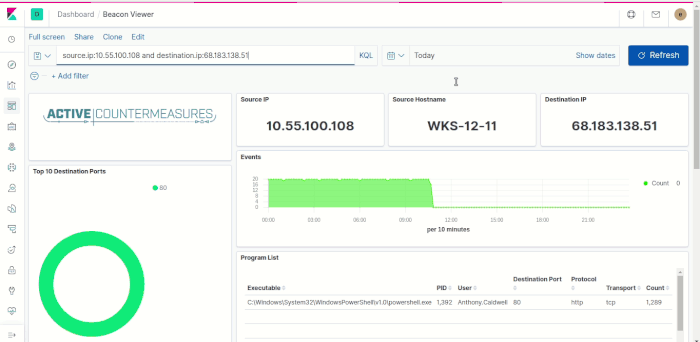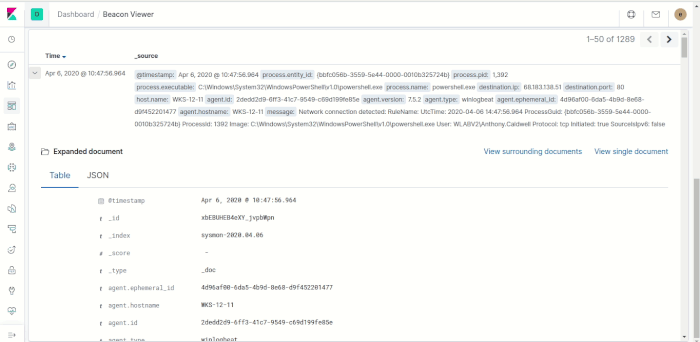
BeaKer is a separate module, and requires one to install the agent on Windows systems and a collection server. The “install_acm.sh” script used for AI-Hunter will help you set up the collection server. For more information, see “BeaKer Integration” in the User Guide.
Since AI-Hunter included the ability to define custom investigation sources, we’ve had users that have added a large number of them. You can now have nested investigation sources in the drop-down menu on IP addresses, allowing you to organize your links. For more information, see “Customizing Investigation Sources” in the User Guide.
Oh, and one more thing (*). Almost everything we’ve published about AI-Hunter assumes that you have a Zeek sensor feeding logs to it. There are some sites that simply can’t run Zeek for policy, architecture, or performance reasons. We have an alternative called Active-Flow.
A few of our developers have put in a massive behind-the-scenes effort to allow AI-Hunter to ingest Netflow version 9 records generated by one or more routers or switches in your environment. The ingested database can report on some – but not all – of the things you’d see if Zeek was providing the raw data feed. For more details on the difference between the approaches, please see the “Differences between Zeek-sourced and Netflow-sourced data” section in the AI-Hunter user guide.
If you’re unable to run Zeek and would like to try Active-Flow, feel free to get in touch with support . We’d be happy to work with you.
This newest version of AI-Hunter is available for download now. For details on how to install it, please see the Install Guide PDF included in the tarball or the Documentation section of the portal website. If you run into any issues, feel free to contact us.
Enjoy and Happy Threat Hunting!
– The Active Countermeasures Team
*H/T to Steve Jobs
Wednesday - 04/01/2020
What do you get when you place a group of top-notch programmers in front of their computers for a month with all the pizza and mountain dew they can ingest(*)? AI-Hunter version 3.7.0!
In this release we focused on customer requests and usability features:
New Features
- Add IP address search capability to the Long Conns, Certificate, Client Signature, and Strobes modules.
- In the Deep Dive module, you can now Pivot! While looking at the deep dive display you can now select one of the IPs around the circle and ask to show a Deep Dive for the new IP by clicking on the “P” (pivot) icon. As an example, this lets you start with an internal IP, find a remote IP that looks suspicious, and immediately switch to a view of the remote IP to see any other internal systems to which that remote ip has talked.
- Whenever we display internal IP addresses, we include their domain names when available.
- AI-Hunter now includes support for Themes – changing the display colors. In this release we add a “daVinci Mode (light)” theme that can be easier to read. To try it out, see the Themes menu under Settings (Gear icon on the dashboard tab)
- In the drop-down Investigation Menu on IP addresses we added “Copy IP to clipboard” so you can easily paste the IP into other programs.
- RITA and AI-Hunter now support Zeek logs in JSON format. This means that Security Onion users no longer have to modify their log configuration.
Minor Changes
- The Rare Client Signature scoring now adds 10 points if any Rare Client Signatures are found, 0 if not. Previously it was adding 5 points for each signature, which skewed the results for some systems if multiple rare signatures were found.
- Additional checks for free drive space and system features.
As always, there are additional bug fixes and other minor changes that happen behind the scenes.
This newest version of AI-Hunter is available for download now. For details on how to install it, please see the Install Guide PDF included in the tarball or the Documentation section of this website.
We encourage you to give it a try! If you run into any issues, feel free to contact us at [email protected]
Enjoy and Happy Threat Hunting!
– The Active Countermeasures Team
* No programmers were harmed in the making of this release, though one QA engineer did get tired of pepperoni.
Wednesday - 01/22/2020
AI-Hunter 3.6.1 is out!
This release is focused on fixes and smaller features. We hope you’ll give it a try!
New Features
- When looking at databases in the database listing, we show the start and end date/time stamps for that database. When a sensor is misconfigured or can’t reach the AI-Hunter server for some reason and logs are no longer flowing, the timestamps will show you that the database has old data.
- We’ve extended the thresholds on the Long Connections and DNS tabs so you can set larger minimums to see just the longest connections or just the more common dns objects. Additionally, we’ve changed the default thresholds to decrease both page load times and the number of low-value results shown.
- Ubuntu Linux 18.04 is now a fully supported OS.
Bug Fixes
- When installing a new Bro/Zeek sensor, the install script in 3.6.0 was unable to find the ja3 plugin needed to fingerprint TLS connections because of file reorganization at the file repository. This has been fixed in 3.6.1.
- There are a number of cosmetic fixes in the installer.
- On the beacons page, the metric bars now fit in the scorebar boundaries.
- Threat Intel exported CSVs now include fields that were missing.
- When clicking a dashboard score the filtered search results displayed will be an exact match to the original IP instead of a partial match that could show unrelated results.
Notes
As always, there are additional behind-the-scenes fixes.
If you have done a new install of Bro/Zeek since November 14th, 2019 we strongly suggest you upgrade to 3.6.1 to install the missing TLS fingerprint plugin. If that’s not the case, you can upgrade AI-Hunter if you’d like one of the new features or are running into one of the bugs.
Enjoy!
For details on how to install it, please see the Install Guide PDF included in the tarball.
Tuesday - 12/17/2019
We’re proud to announce version 3.6.0 of AI-Hunter (the “Early Present” release). Our (elves) developers have been putting in extra hours to give new functionality and fixes, and we hope you enjoy it!
New Features
- Custom Investigation Sources
When looking for more information on a particular IP address, you’ve had a drop-down menu that sends you to AbuseIPDB, apility.io, or the Deep dive with details on that IP. We’ve included several new sources in this release. Also, you can define your own – perfect if you have an internal web site or external service you depend on for IP address details. For more details, see “Customizing Investigation Sources” in the User Guide. Teaser – AI-Hunter subscribers will be getting early access to a brand new investigation source; look for an email in early January!
- Alerting
Previously you got alerts in syslog and Slack when a system first showed up with a too-high threat score, when that score increased, and when that score decreased. Now you can individually tune whether you want to get alerts on a score increase or decrease. For more information, see “Modifying threat scores and Configuring alerts” in the User Guide.
- RITA
AI-Hunter now includes the latest release of RITA, version 3.1.1. This includes bug fixes as well as a new import flag that allows you to reimport an existing database.
- Whitelisting
Previously, you could whitelist entries completely from the Dashboard. However, whitelisting elsewhere in AI-Hunter would not recalculate the Dashboard host scores. With this release if you whitelist a host elsewhere, in Beacons for instance, it will now update that host’s score in the Dashboard.
- Threat Intel
We’ve added some more background info on why a host is listed there, including the fully qualified domain name and the type of traffic being sent to the blacklisted host.
- Databases
If you have more than 1 sensor and want to view all data from all sensors at once, we include a new tool that pulls all the data from all sensors into one called COMBINED__0000. For more information on this, see the “View all sensors in a single database” section of the User Guide.
Note About the Install
During the installation you’ll be prompted to upgrade your existing databases, and asked how many you’d like to upgrade. This upgrade only applies to the dated snapshots (“-rolling” databases will be upgraded automatically over the next 24 hours), and the only change is applying the current whitelist to the Dashboard in each. The upgrades can take some time, and while this is happening, AI-Hunter will not be available.
If you choose not to upgrade a particular database the new whitelisting features from this release won’t apply to the dashboard, but your databases should otherwise function as normal. For that reason we encourage you to only upgrade the dated databases that you expect to work with. If you never access the dated snapshot databases, you can enter “0” for the number of days to upgrade. If you do upgrade some, we encourage you to upgrade a small number of recent databases.
Additional Fixes
- Database Upgrades
During the install, if you have any databases whose format has changed, the install will prompt you to upgrade them automatically.
- User Interface
When you whitelist an IP or switch views on the Beacons page, you’re no longer sent back to the first page of results.
When host names are truncated, we now have a popup box that will show the full name.
Notes
As always, the release includes lots of smaller cleanups and bugfixes. Please give this a try, and let us know what you think!
For details on how to install it, please see the Install Guide PDF included in the tarball.
Thursday - 09/19/2019
We’ve provided a new release of AI-Hunter, which is in your Account under Downloads. Version 3.5.0 includes the following:
- “Blacklisted” is now renamed “Threat Intel” to match the intent of the feature.
- The log transport mechanism now handles Bro logs in non-default directories.
- Rita has been updated to version 3.0.6 .
- “rita import” can now import individual files (in addition to directories that it could import in previous versions).
- Additional cosmetic fixes, cleanups, and error checking related to syslog alerting, configuration defaults, the installer, database copies, and the aih_status script.
If you’re installing AI-Hunter for the first time, we encourage you to use this new version. If you’re on version 3.4.0 (*) we encourage you to upgrade to 3.5.0 as soon as convenient as this will resolve some fairly important bugs in 3.4.0. If you’re running version 3.4.1, 3.4.1 includes these fixes as well so this is not a critical upgrade, but we do encourage you to upgrade when time allows.
We do have one known issue with 3.4.1 and 3.5.0. In the Blacklist/Threat Intel tab, the box displaying additional information about IP addresses is not showing the correct details. As a temporary workaround, we encourage you to use an external web site to see additional details. Click on the IP address in question and you’ll see a drop-down menu; click on apility.io and you’ll be taken to a page with these details.
* To see your version, log in to AI-Hunter, select the Dashboard, click on the Gear icon in the upper right, and click on “About”.
Monday - 08/19/2019
We’ve provided a new release of AI-Hunter, which is in your Account under Downloads. Version 3.4.1 resolves two bugs that made it into 3.4.0:
- After upgrading to 3.4.0, new data is not flowing into the rolling databases. This came out of a database change. The bug wasn’t apparent until after release and further QA testing.
- A second error in the snapshotting process meant that instead of trying to create a new snapshot named after yesterday’s date, it was trying to create the same snapshot name every day.
We encourage all 3.4.0 users to upgrade to this version as soon as possible. If you’re on 3.3.0 or below we still encourage you to upgrade to 3.4.1 as, in addition to the above bug fixes, there are many usability and workflow improvements from 3.4.0 that have been carried forward.